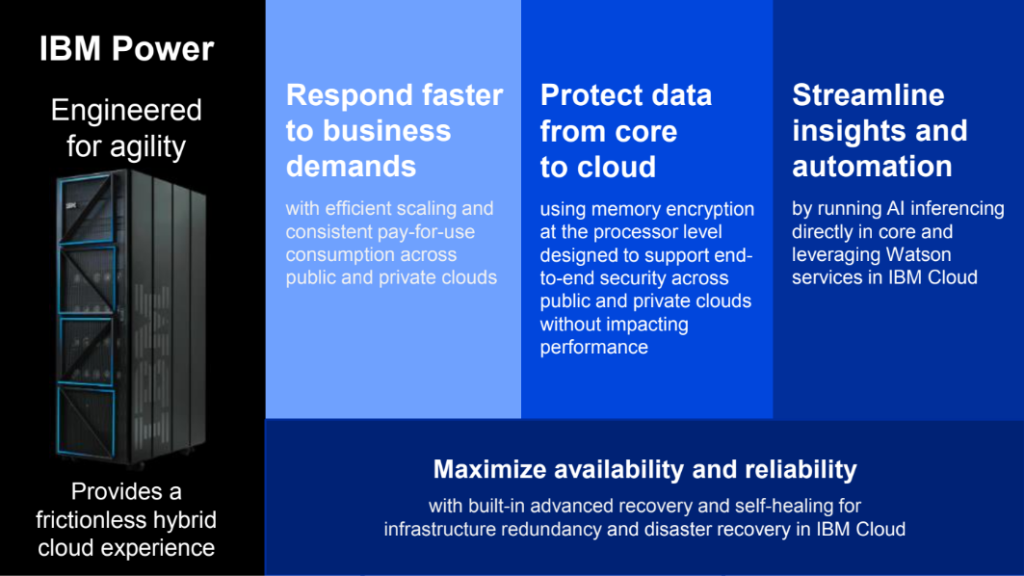
This point of view paper considers the benefits of the IBM Power10 Chip for its security and performance advantages that have been developed over many years and versions. We examine a different viewpoint of what the biggest security risks are and how the architecture greatly reduces any chance of an attack. To do this, we need to understand the combined capabilities of IBM architecture. We will discuss strategies of its use in the hybrid cloud in a “frictionless” environment. The chip set and design are part of the E1080 server platform, which is complemented by the PowerSC for Cloud Security, PowerVM for virtual machines, PowerVC for advanced virtualization, cloud management, and Ansible (task) Automation.
A supplemental section describes virtualization and containerization. This offering from IBM is the most secure platform available on the market today to offer performance, while avoiding external and internal Cyber Attacks.