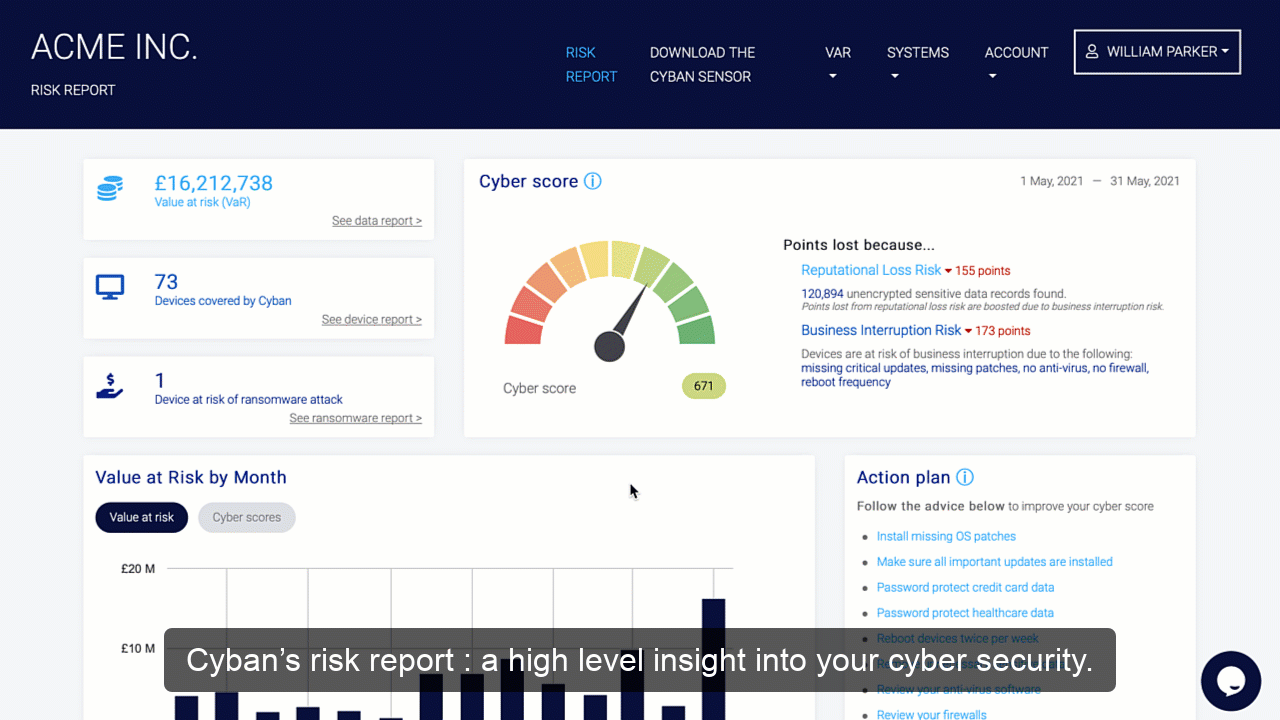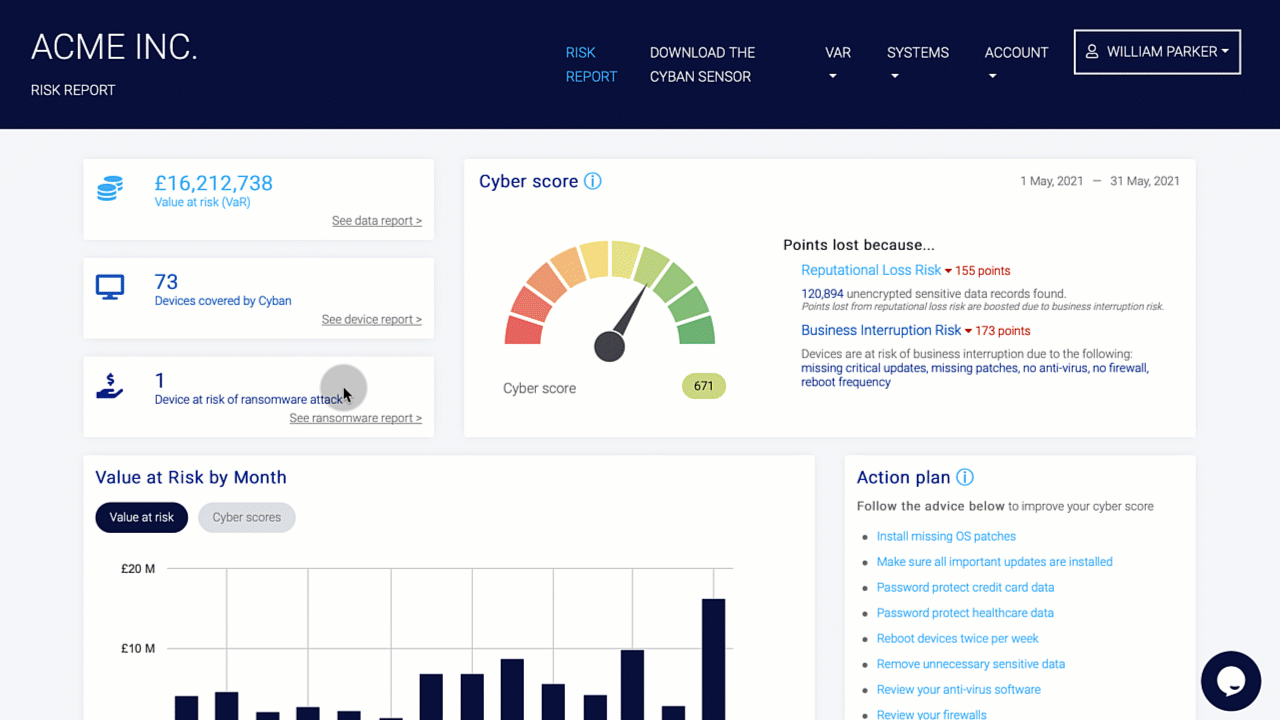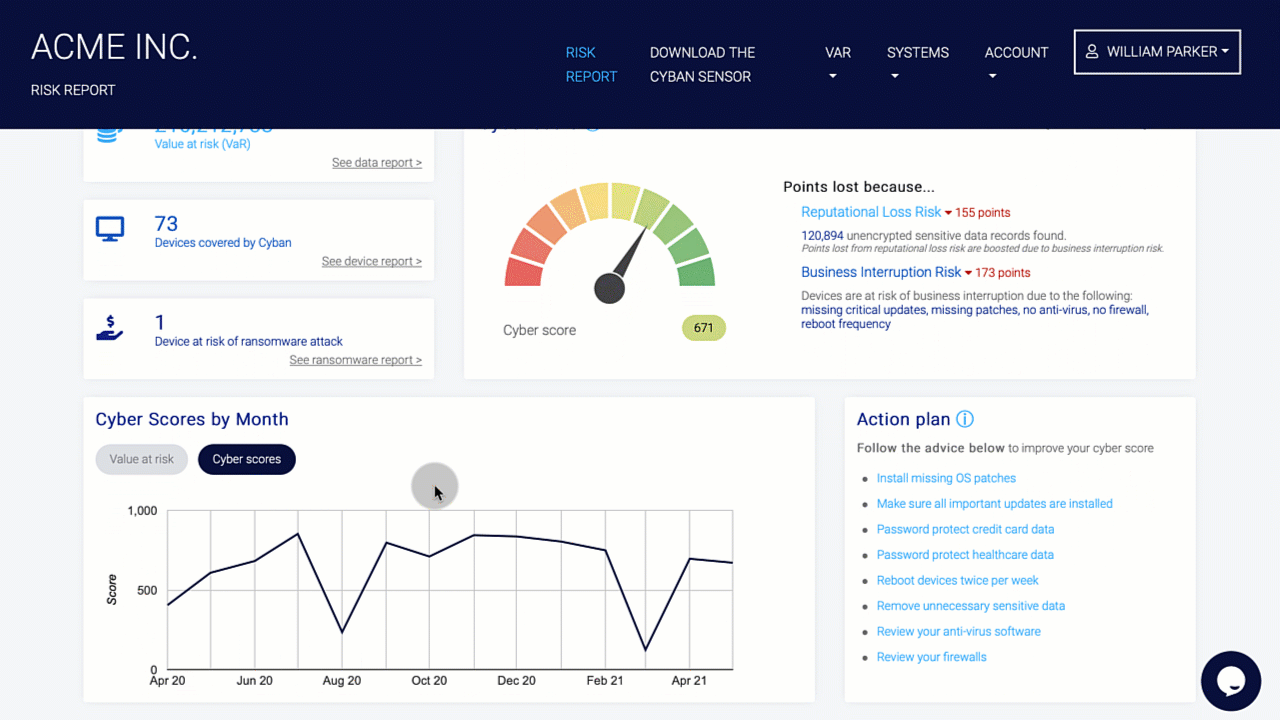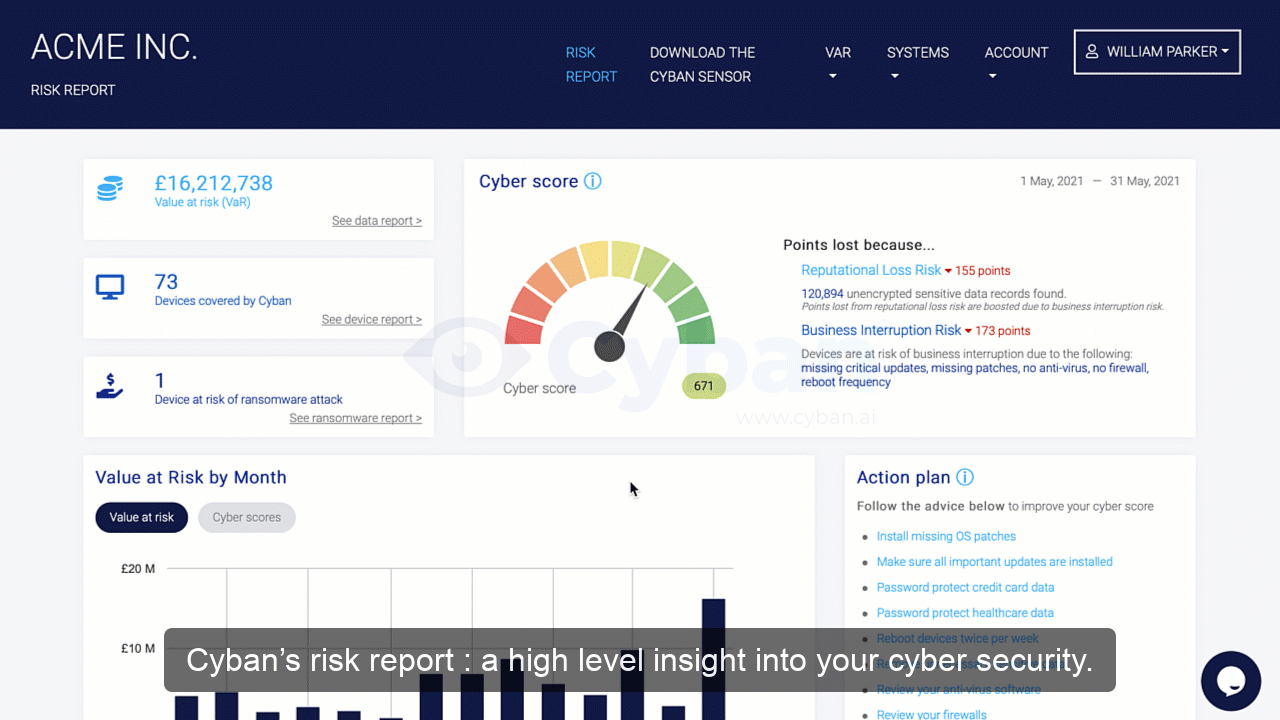
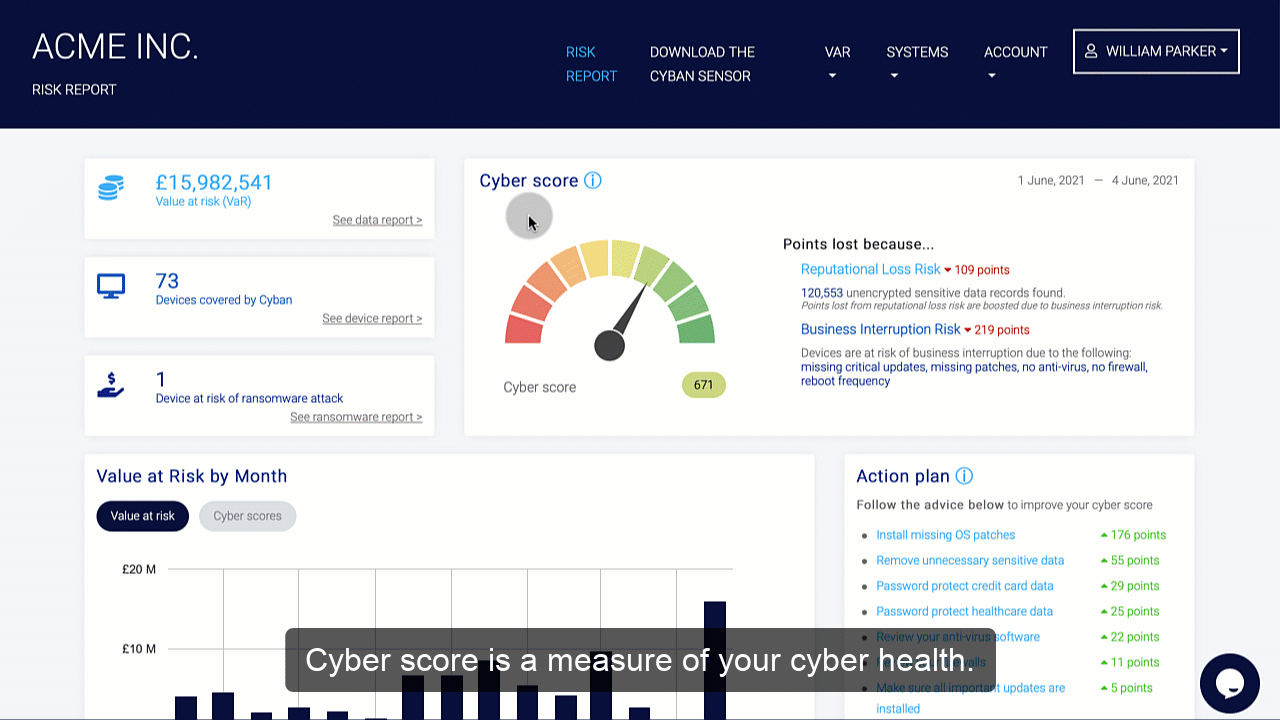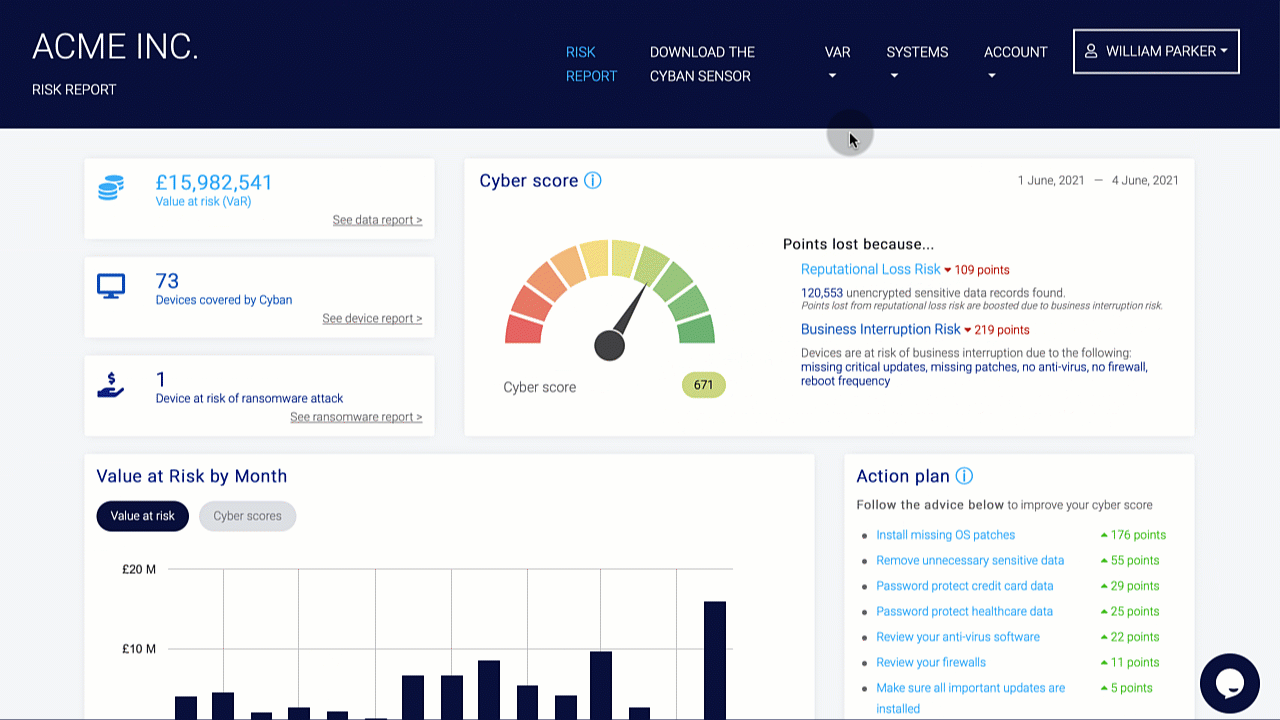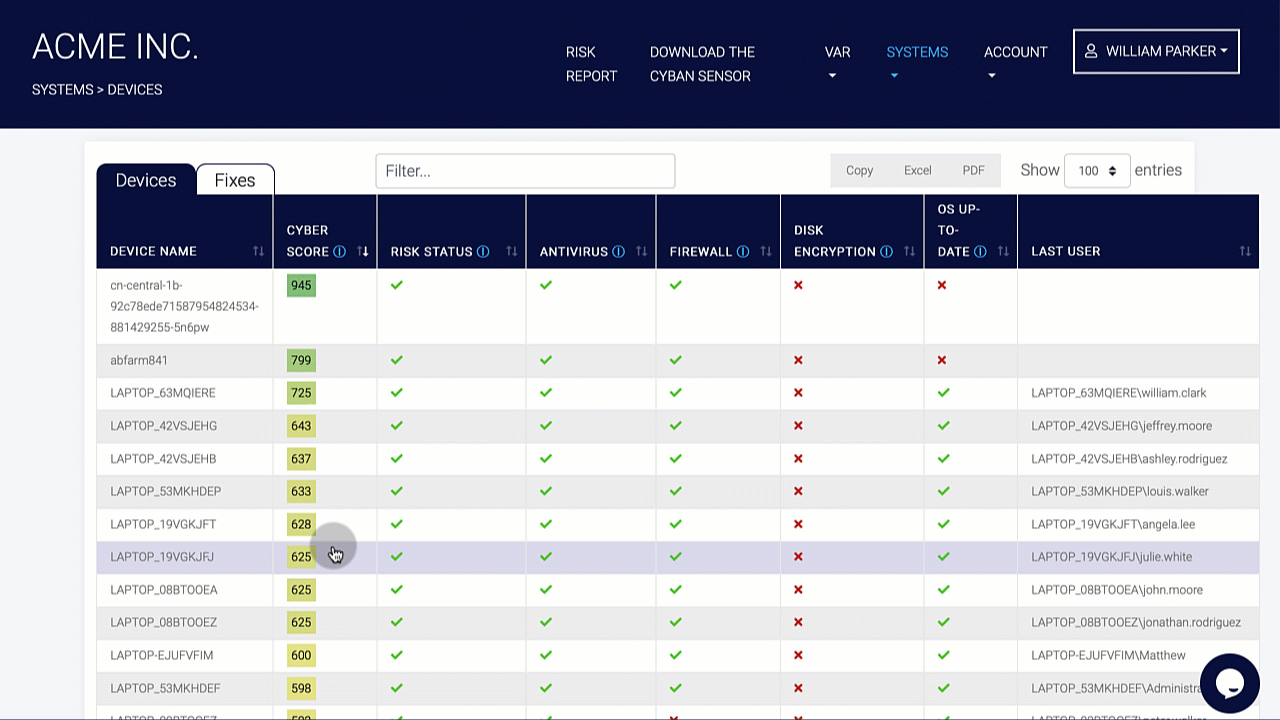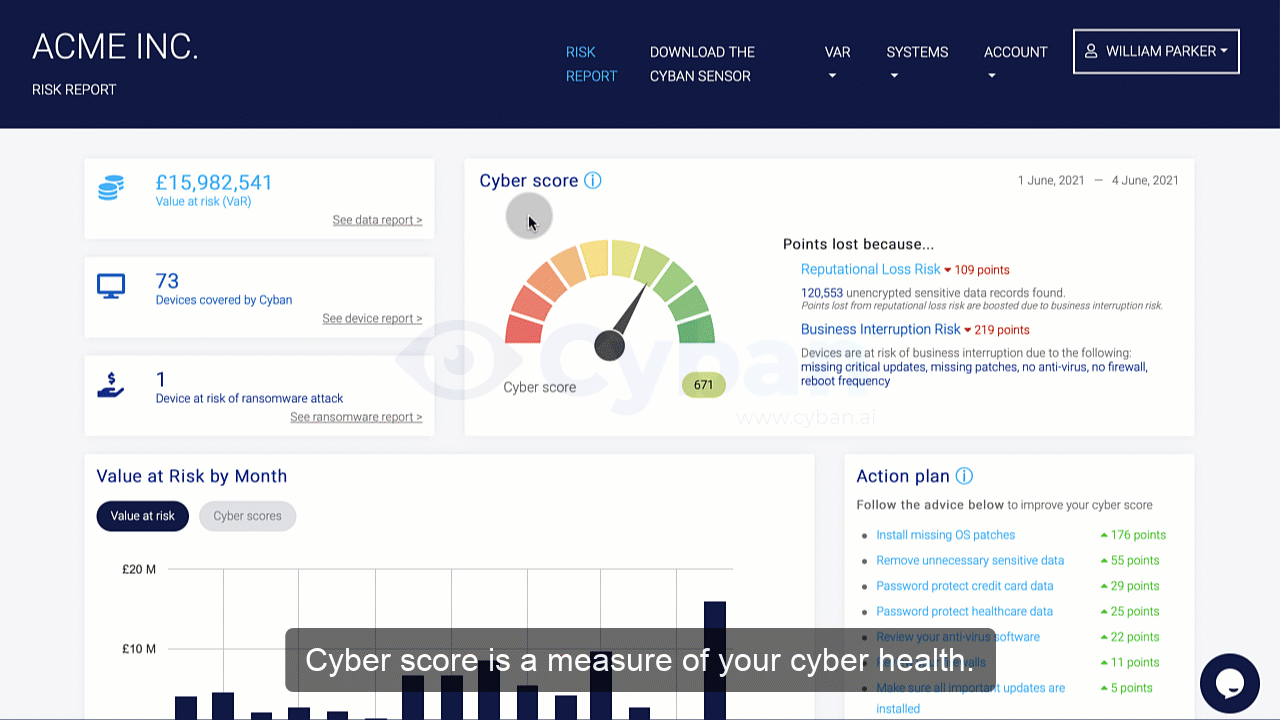
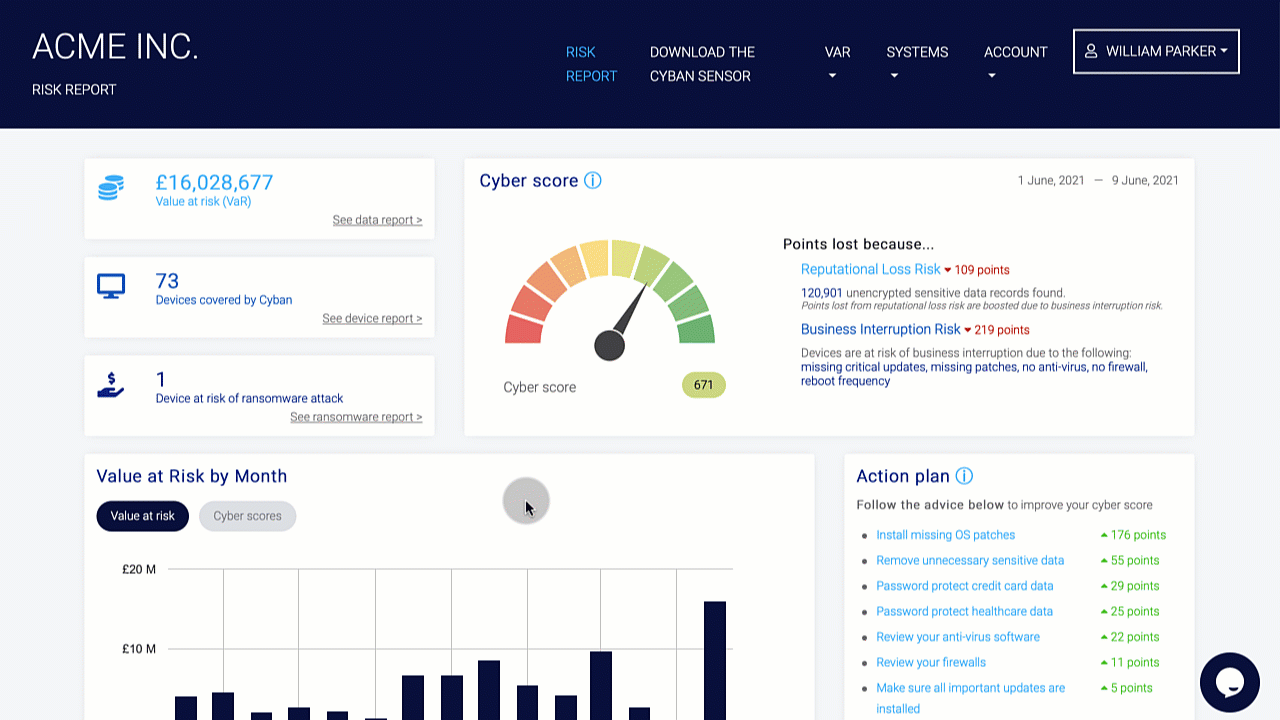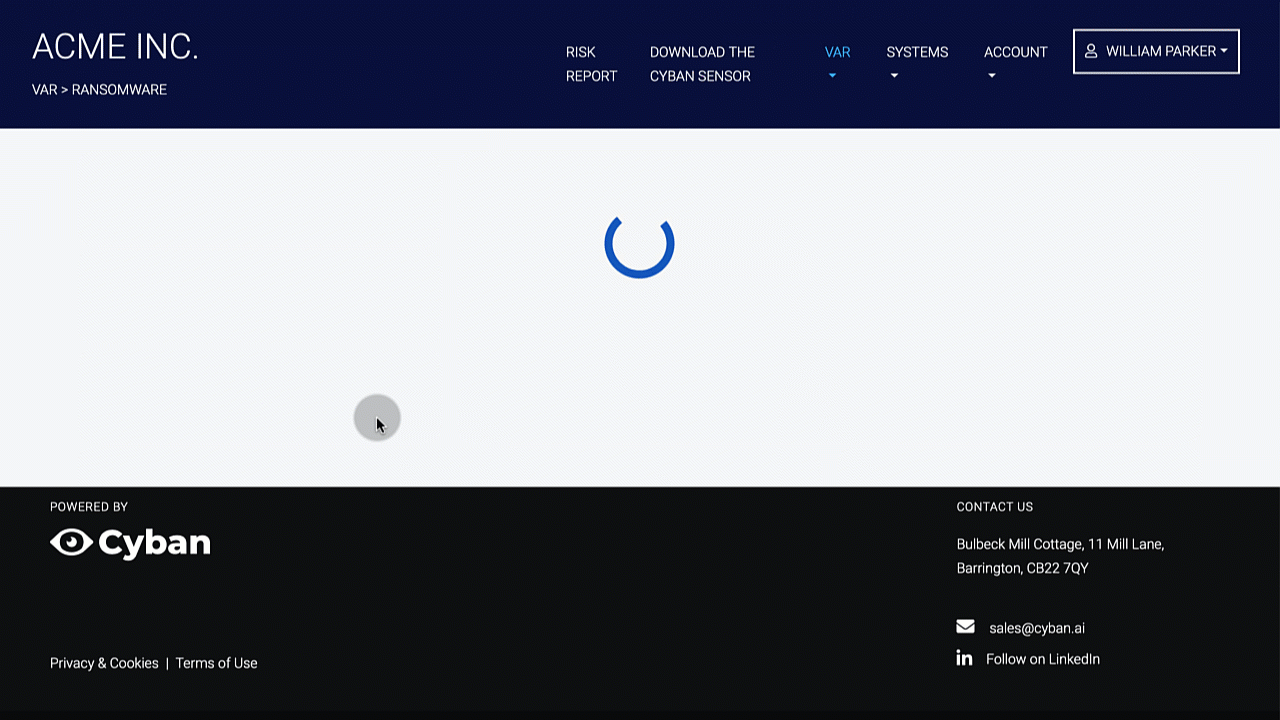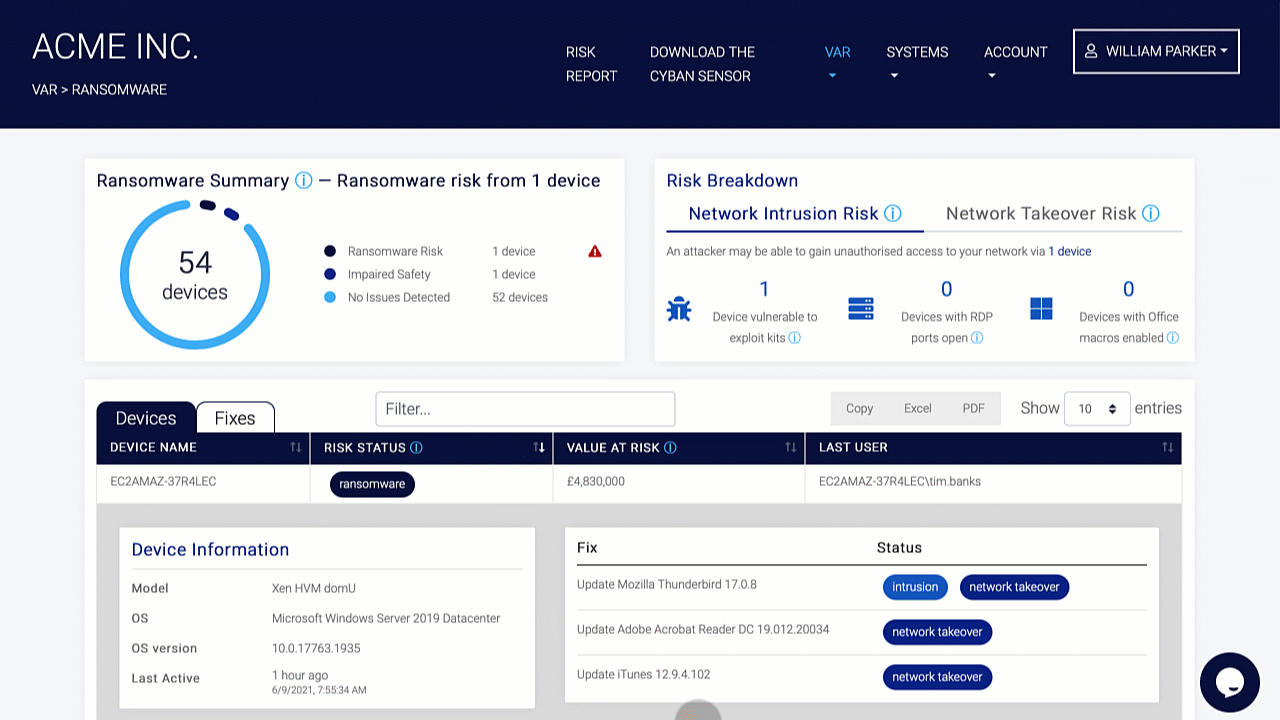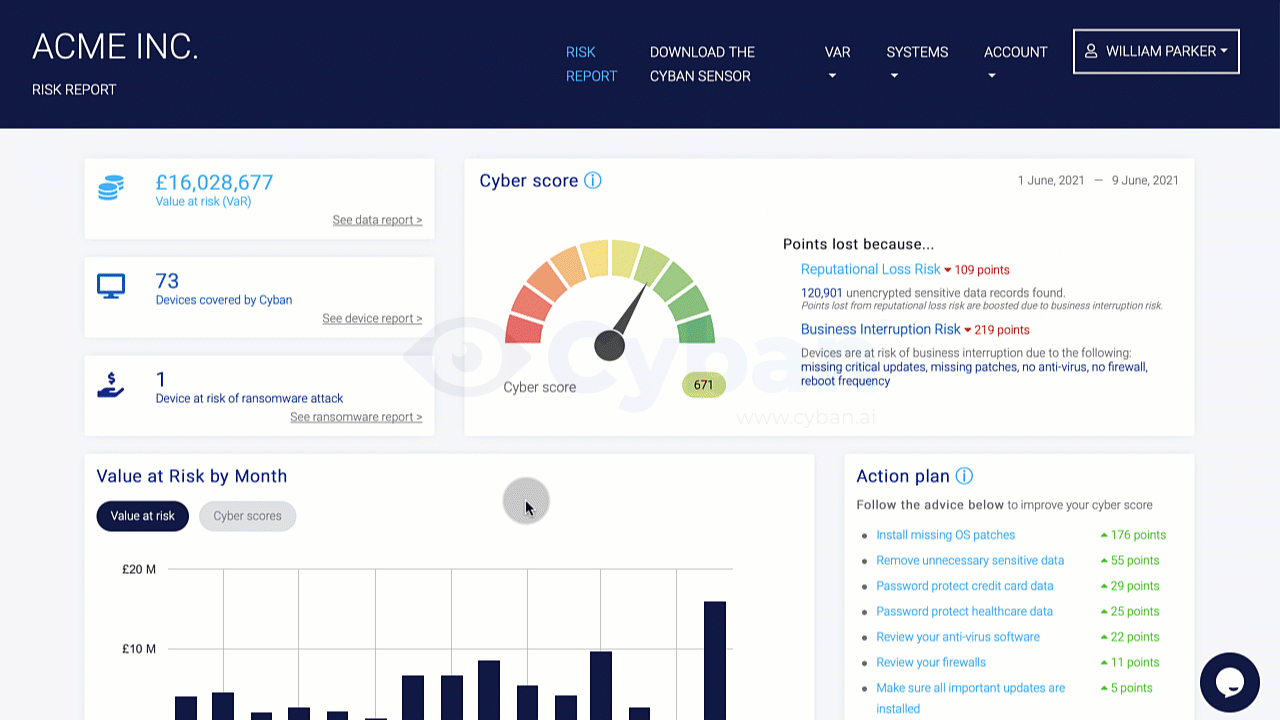
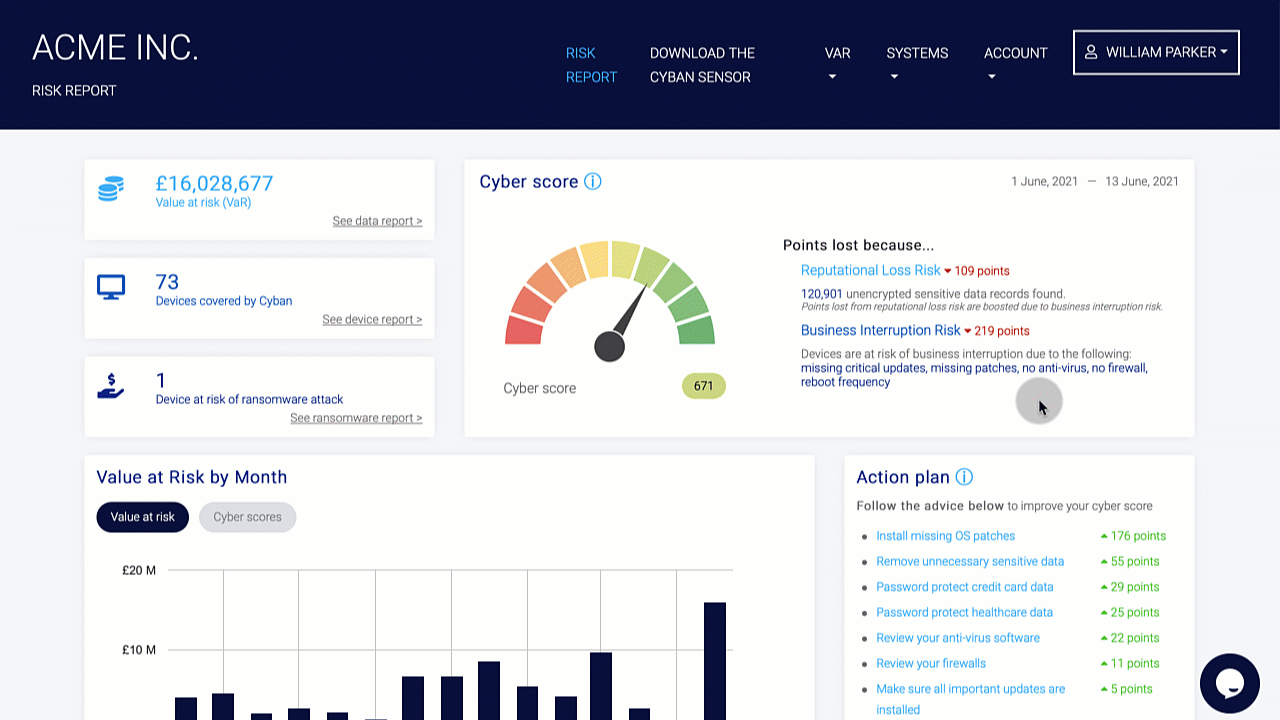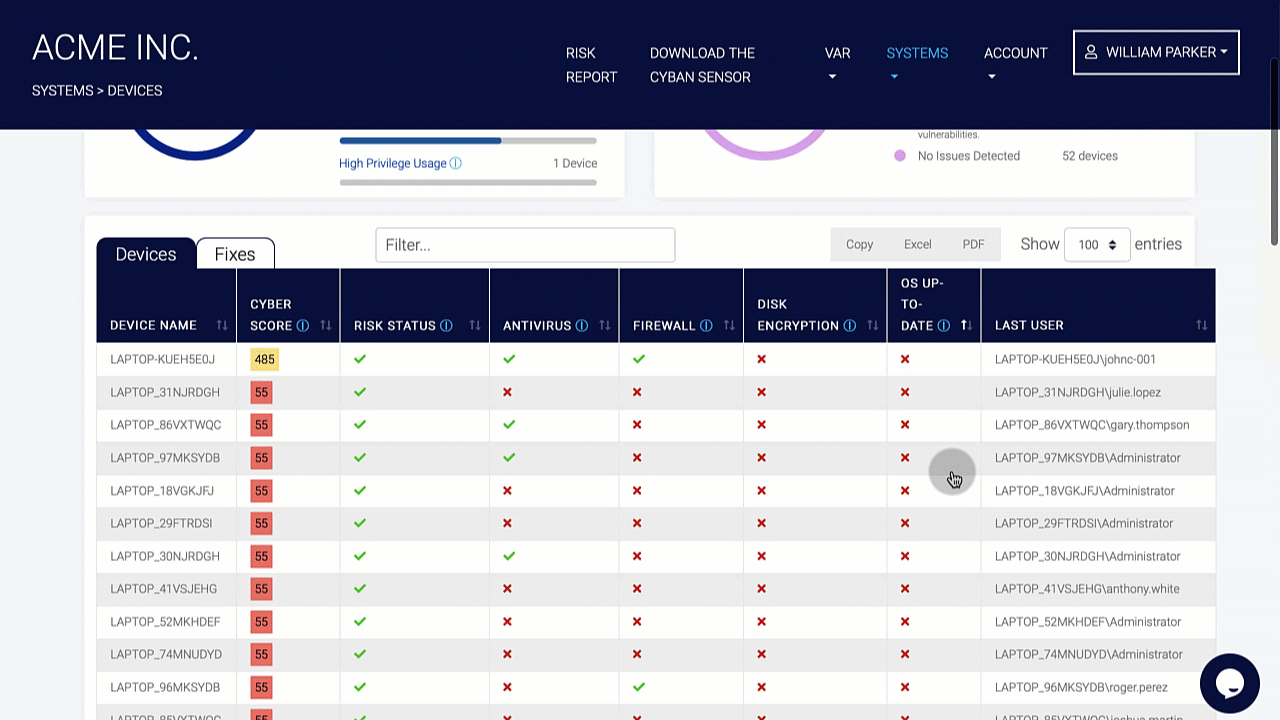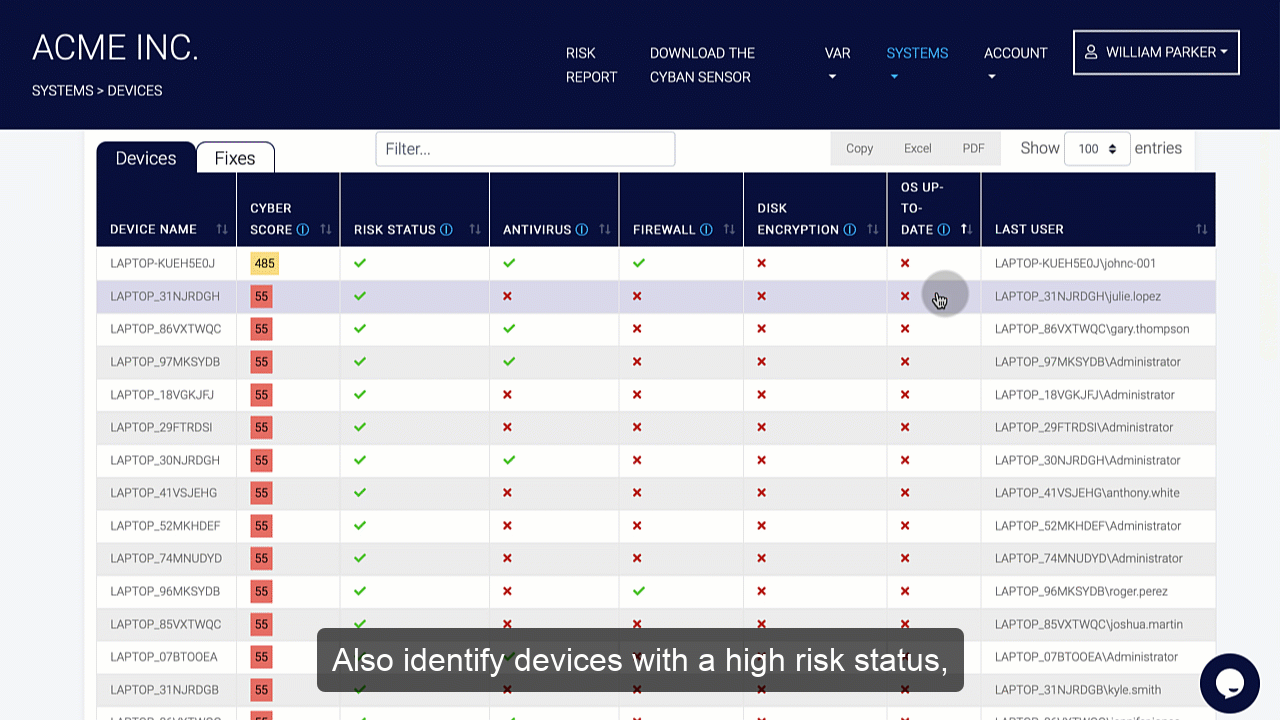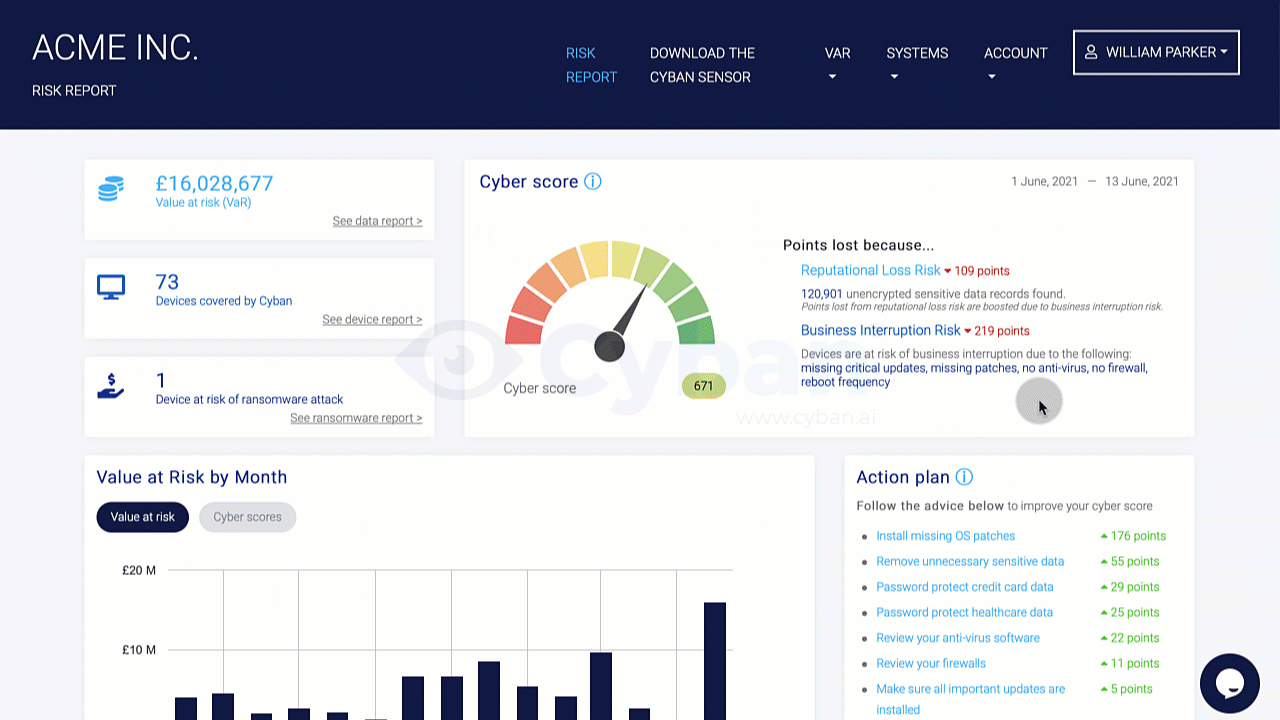
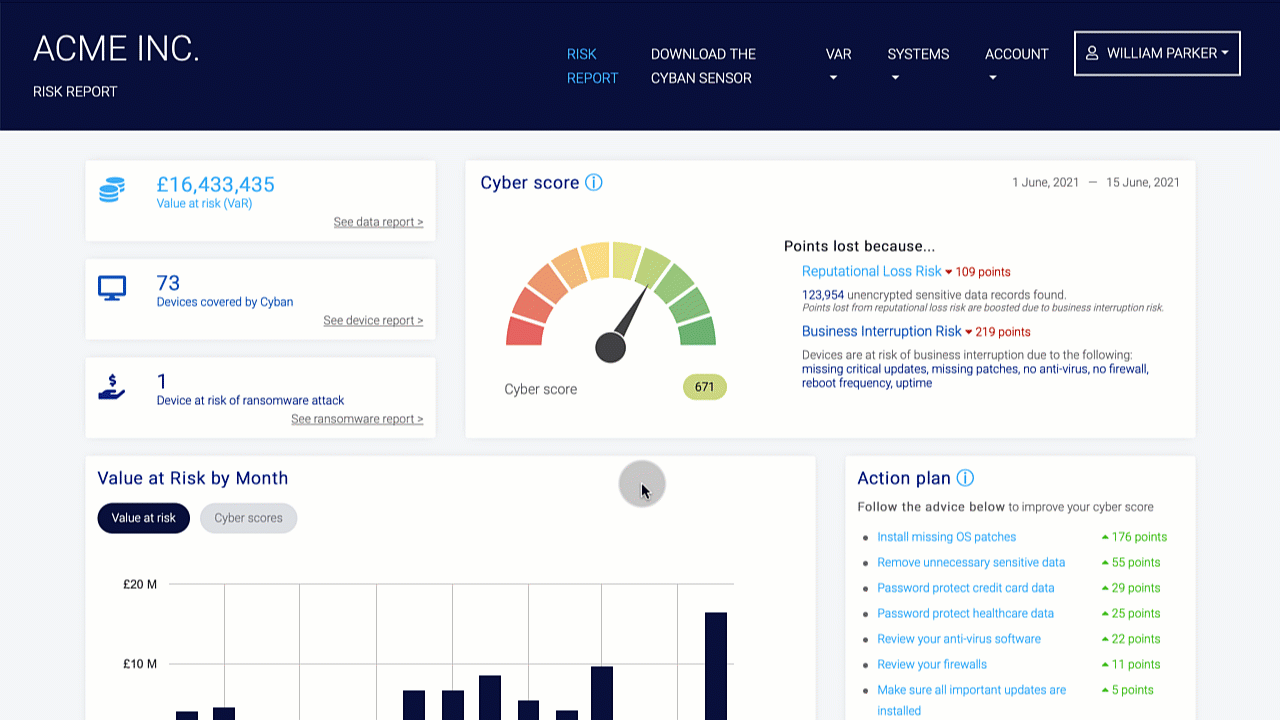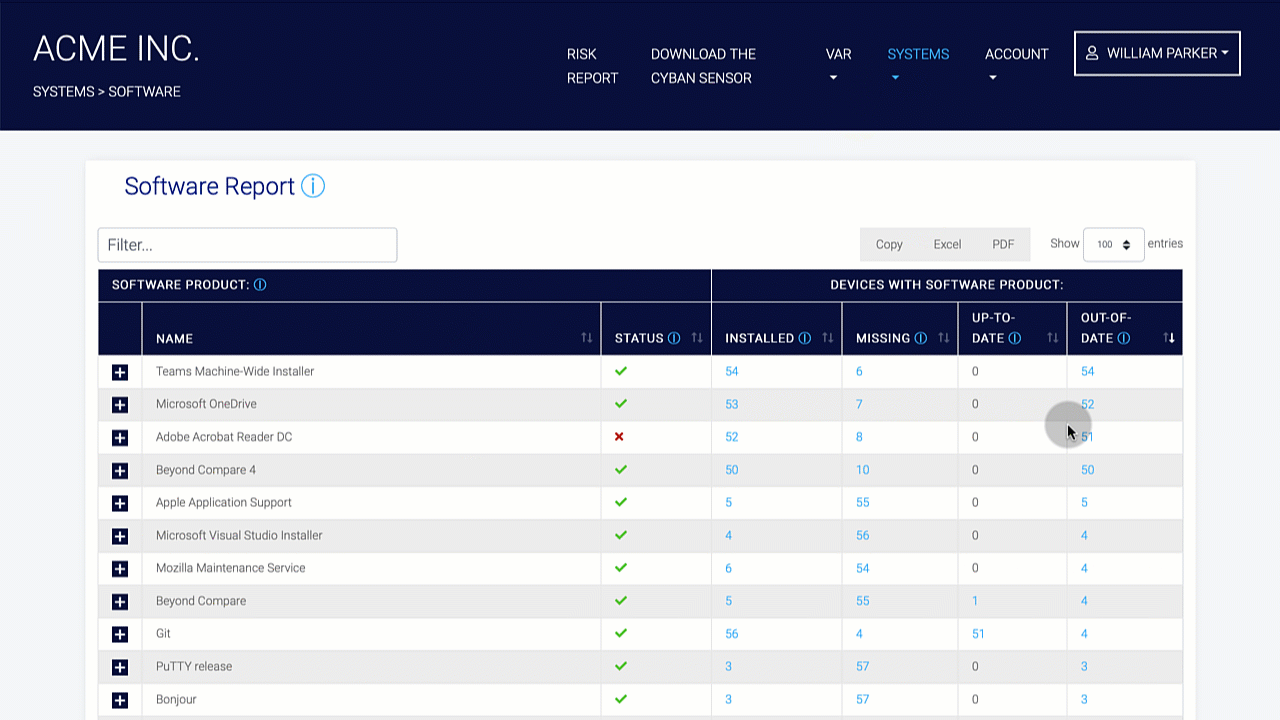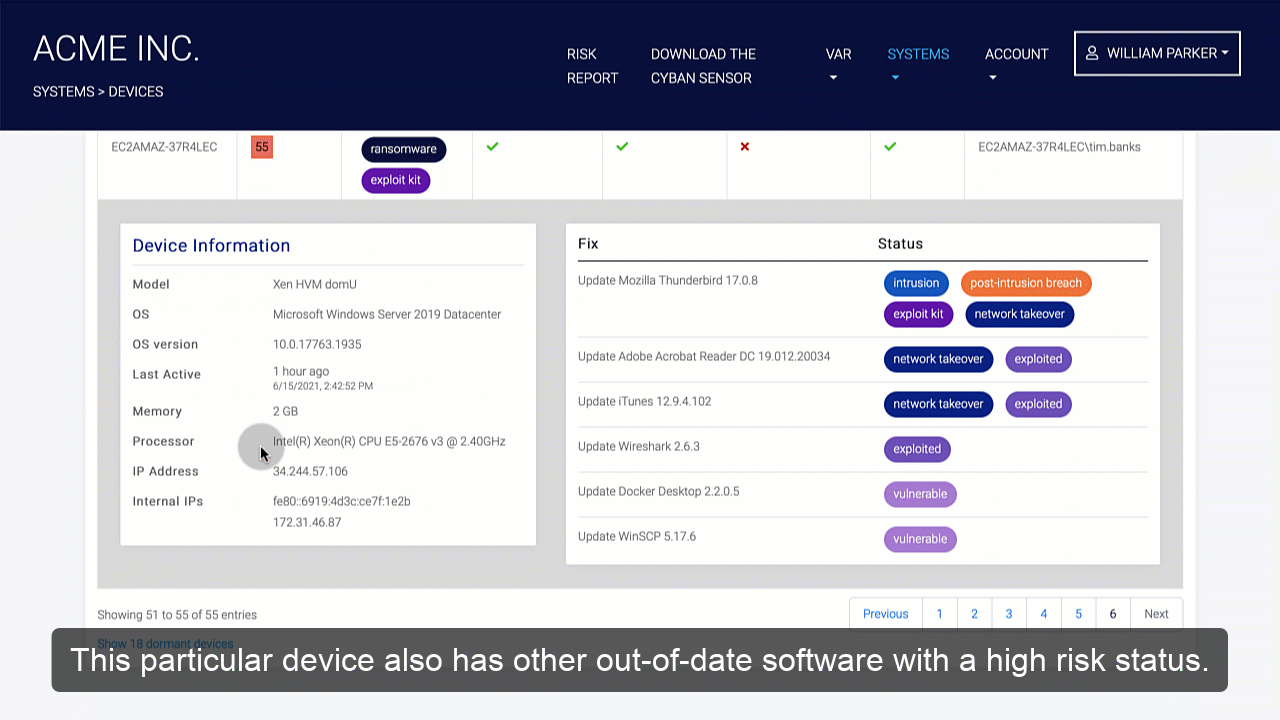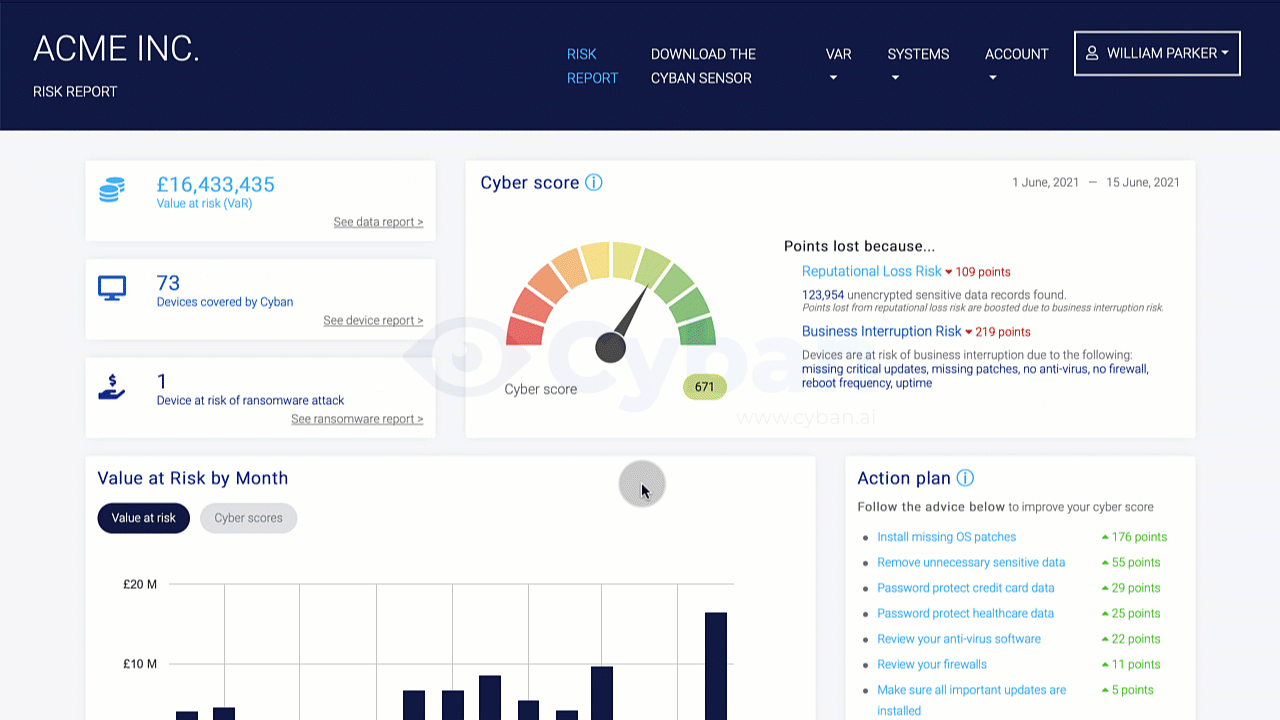
Organizations should conduct a risk assessment of their IT environment from all angles. The assessment’s goal is to find vulnerabilities that internal and external threats could exploit and place the company at extreme risk.
Vulnerabilities, dangers, and risks in IT protection are constantly changing. It is important for businesses to monitor their environment on a regular basis for potential business risks. Risk is defined in the sense of IT security as a factor that compromises the confidentiality, integrity, or availability of an organization’s data.
Perimeter External Vulnerability Scanning, Cloud Security Audits, Dynamic Web Application Vulnerability Scanning, Certificate Analysis, and Dark Web Vulnerability Correlations are all used to find vulnerabilities.
These testing tools focus on problems such as device hardening and misconfigurations. Organizations can harden the protection of their perimeter and underlying structures by addressing these issues. Patching, interface updates, and protections are not enough to remove risks, so they should be included with a cyber insurance policy. Cyber insurance protects the company from the financial consequences of a cyberattack.
One of an organization’s most vulnerable areas is passwords. According to a new Gartner report, they account for nearly half of all cyberattacks. Imagine lowering cyber risk by 50%, which will please the Board of Directors. Destiny Corporation can assist you in avoiding threats.